What is Automation? Every office has those menial tasks that nobody wants to take the time to do, but really need to be done at some point. Fortunately, as technology has advanced, so has the capability for these tasks to be completed with minimal human engagement. Automation (technically, business process automation) is simply the use of technology to simplify and minimize the amount of work and attention your human resources need to contribute in order to reach an objective. As automation has received a bit of a bad break as a job killer, it is important to clarify that the kind of automation we generally talk about is intended to lighten the rote responsibilities of your employees, freeing their time to focus on other, more productive tasks and concerns. When used in this way, business process automation can help boost your employees’ job satisfaction, consistency, and efficiency (although the job-killing reputation that automation has garnered might lead to some resistance at first). Not sure how you might put it to use in your operations? We have a few suggestions that you may find intriguing. How to Leverage Automation When all is said and done, automation could conceivably assist with any task. However, we want to focus on the ways that will really provide your business with the most value, so mull over some of these applications (again, just some of your potential opportunities). Customer SupportHow much time is spent answering calls, or emails, or Facebook messages, all asking precisely the same question? Chances are, too much. That’s why many automated customer support options are so useful – they give you an alternative way to provide support that can often resolve your contact’s quandary without involving you or your employees. This kind of vetting reserves your employees’ attention to issues that really require it. ComplianceMany industries are subject to assorted requirements that concern different aspects of their operations, passed down by the government or by the industry itself. Automation allows you to set procedures that meet the prescribed guidelines to appease regulators, saving you from further trouble and effort later. CommunicationThere are a lot of moving parts involved in any business (especially if automation is put in use), so there are going to be certain people who need to be kept in-the-know. These people may be internal resources, or operate outside of the business. This even includes clients and customers. Regardless, automation can help ensure that there is always clear communication, without anyone having to remember to send a message. Naturally, there are far more ways that your business’ operations could be automated behind-the-scenes, so don’t hesitate to reach out to us and discuss what your options might be! Our professionals are here to help. Call (831) 758-3636 today.
This can create some difficulties. How often have you found yourself locked out of one of your accounts because you accidentally put in the password for another one? Or one that you had used for that account in the past? These kinds of issues can be insanely irritating to deal with, which is why password management systems have become so popular among businesses. Here, we’ll review the three primary reasons that you should consider password management. Less to Remember A 2007 study states that, on average, a computer user typically had about eight password-protected online accounts. Considering all of the services and platforms that have been developed and become popular in the last decade, it isn’t hard to imagine that this “eight” has almost assuredly swelled considerably. This means that the pressure that comes from remembering a sufficiently complicated password for each account has similarly swelled. While the human memory can be trained to astounding limits, that requires some pretty intense training… are you suggesting that you’re willing to invest in this training for each one of your employees? Unfortunately, most businesses can’t realistically make this commitment. That’s okay, because a password manager accomplishes effectively the same thing, while giving you control over your own resources and assets. All a user needs to remember is a single master password, and they will be able to access all of the passwords they need to do their job. Security is Easier to Maintain So far we’ve reviewed that it is important to use a variety of passwords that corresponds to the variety of accounts you have, but we haven’t really touched on why. Doing so is pretty simple… just put it in the scope of the private user. Would you rather have a credit card stolen, or have all of your credit cards, bank accounts, medical records, property holdings, investments, and social media accounts stolen? While neither option is ideal, the latter one is clearly worse, and is exactly the kind of scenario that comes from recycling passwords. A password manager protects you from the temptation of recycling passwords, as well as the temptation to make them easy to guess. As a result, your overall password strategy remains secure, the potential for escalation being significantly reduced. Improved Management There will almost assuredly be varying needs in your business, as far as access to documents and resources is concerned. However, if there is a particular account that needs to remain secure, while still being accessible to your staff, a password management system can be extremely helpful. Via the password manager, you can manage your users’ credentials. Controlled by the responsibilities of each user as per their role, you can prevent your users from even seeing the credentials while they are putting them in, boosting your security even farther. Want help improving your security, either through a password management system or some other means? Reach out to SRS Networks at (831) 758-3636 to start a conversation.
Set Up Your Desktop When you begin to use a new operating system, it all seems a little bit foreign. In Windows 10, most users that have been computing with Windows for some time will have no problem with the set up. There is a desktop, a start menu, a taskbar. It looks a lot like Windows 8.1, Windows 7, and Windows Vista before it. If you are coming over from those other versions, you will notice that getting started might be a little confusing. Firstly, the system shortcuts found on those versions of Windows don’t appear when you first start up your new version of Windows 10; and, when you click on the start menu, you won’t get immediate access to a lot of the familiar icons you have come to know. My Computer is gone, no Control Panel, in fact most of the options outside of the Recycle Bin are nowhere to be found. This can be pretty intimidating for the novice user. It doesn’t have to be. Setting up your Windows 10 Desktop is simple. It really takes changing a couple of settings and you will be right at home. The first step in making a Windows 10 desktop is to change your theme. To do this you can right click and click on Personalize. In this menu, you can change most of your display settings. For our first customizable tip you need to direct your attention to two settings in this menu. The first is the first screen you encounter: Background. In this menu you can set the background image/color and how that image or color is represented. Nothing personalizes a Windows 10 experience quite like your own choice of background image. The second option that we think will make a big difference to a user is under the Themes menu. If you look down the page a bit, you’ll see the option called Desktop icon settings. Here a user can show/hide the desktop apps that we mentioned earlier. Do you want a shortcut to the control panel? Are you used to navigating from My Computer? You can add these apps to any desktop experience. Set Up Your Taskbar The taskbar is especially useful in Windows 10. Not only can you access your Start menu, notifications hub, and task view, you also have access to search and the built-in Cortana virtual assistant. You can access open applications, and better yet, pin popular applications to the taskbar. This gives you quick access to your most popular applications. It is fully customizable. To customize the taskbar, simply right-click on the taskbar and you will be brought to the Taskbar menu. It is actually in the same Settings page, so if you have it open from before, you can just click on Taskbar at the bottom of the menu. On this page there are several options that you can change for the taskbar. You can lock it in place, you can hide it when it’s not in use (in both desktop and tablet modes), you can toggle the mouse-over preview, and more. As you scroll down, you can click on Select which icons appear on the taskbar to customize your experience further. If you would like to pin your favorite applications to the taskbar, you simply find the tile […]
Samsung Galaxy s10 Plus Widely regarded as the best phone on the market, the Samsung Galaxy s10 Plus improves on the remarkable Galaxy s9 Plus across the board; improving on form factor, processing, camera, and battery. The device is Gorilla Glass 5 on top of an aluminum frame and weighs in at 6.17 oz. The display comes in at 6.4 inches and uses most of the phone’s available real estate. The form factor of the device has had a bit of a renovation, featuring sharper edges than previous models. Inside the device, the Galaxy s10 Plus has a Qualcomm Snapdragon 855 processor with 8-to-12 GB of RAM and storage capabilities that range from 128 GB to a full terabyte. The Galaxy s10 Plus features three rear-facing cameras, including a wide angle, ultra wide angle, and a telephoto option. Samsung also increased the battery to a solid 4,100 mAh. It is shipped with Android 9 Pie, but some carriers already deliver an upgrade to Android 10. Available in Prism White, Prism Black, Prism Green, Prism Blue, Canary Yellow, Flamingo Pink, Ceramic Black, Ceramic White, Cardinal Red, and Smoke Blue this device can be had on most carriers for between $799 and $1,199. Samsung Galaxy s10 PlusBody: Aluminum frame with Gorilla Glass 6 front, Gorilla Glass/Ceramic backDisplay: 6.4-inch Dynamic AMOLED (~522 ppi)OS: Android 9.0 with Samsung One UI skinChipset: Qualcomm Snapdragon 855Memory: 128 GB/8 GB RAM; 512 GB/8GB RAM; 1 TB/12GB RAMExpandable Memory: microSD up to 1 TBCameras: Three back-facing (12 MP, 26mm wide angle; 12 MP, 52mm telephoto; 16 MP, 12mm ultrawide); Two front-facing (10 MP, 26mm; 8 MP, 22mm)Sounds: Stereo speakers, 3.5mm headphone jackBattery (battery endurance rating): 4,100 mAh battery (91 hours)Security: Ultrasonic, under display fingerprint reader; IP 68 resistantMiscellaneous: Nano-SIM, Wi-Fi 6, Bluetooth 5.0, 15W fast charging, wireless charging, reverse wireless charging, NFC, FM RadioOther versions: Samsung Galaxy s10, Samsung Galaxy s10e Apple iPhone 11 Pro Max This year Apple’s flagship is called the iPhone 11 Pro Max and it continues Apple’s dedication to creating elite-level smartphone experience. The iPhone 11 Pro Max is glass front and back, built on a stainless steel frame and providing users a 6.5-inch Super Retina display. Inside the device there is Apple’s proprietary A13 Bionic chip, four GB of RAM, and either 64 gigabytes or 512 gigabytes of onboard storage. The biggest improvement over the iPhone XS are the cameras. Users will have the use of three 12-megapixel lenses including an ultra-wide angle lens, a wide angle lens, and a telephoto lens. The device runs on the iOS 13 operating system and can be had from most major carriers in Space Gray, Gold, Silver, and Midnight Green for around $1,100. Apple iPhone 11 Pro MaxBody: Stainless steel frame with glass front/backDisplay: 6.5-inch Super Retina XDR OLED; 1,242 x 2,688 (~458 ppi)OS: iOS 13Chipset: Apple A13 BionicMemory: 64 GB/4 GB RAM; 256 GB/4 GB RAM; 512 GB/4GB RAMExpandable Memory: NoneCameras: Three back-facing (12 MP, 26mm wide angle; 12 MP, 52mm telephoto; 12 MP, 13mm ultrawide); Two front-facing (12 MP, 23mm; SL 3D camera)Sounds: Stereo speakersBattery (battery life): 3,969 mAh (102 hours)Security: Face ID, IP 68 resistant Miscellaneous: Nano-SIM, Wi-Fi 6, Bluetooth 5.0, 18W fast charging, wireless charging, NFCOther versions: Apple iPhone 11, Apple iPhone 11 Pro Samsung Galaxy Note 10 Plus Years away from the […]
Shadow IT is Bad Let’s face it, most people working today have been using technology for over 20 years. They may not be IT experts (they aren’t), but they aren’t novice users either. They can spot a tool when they see one. For the end-user, finding solutions to their problems in the form of a simple-to-download application, is a no brainer, especially if the person is proficient with the unauthorized software. They won’t think twice before downloading the title. The problem, quite obviously, is that the software being downloaded may have vulnerabilities upon download; and, if it’s allowed to fester without updates on a workstation for some time, will likely have some. Unfortunately, vulnerable software on a network endpoint is a hole in the network itself. We spend a lot of time on this blog talking about cybersecurity, and one of the big no-nos is leaving unpatched holes in your network by not frequently patching and updating software. Since the IT department or managed IT provider handles this process, if they don’t look for a software to update (because they often don’t know it is there), it will likely be a problem before long. What are the potential risks? There are a multitude. They include: A lack of security – Without the visibility and control over network-attached resources, IT management becomes much more difficult. If there is a potential that a piece of software can put a hole in your network, you are compromising the network’s security. Problems with performance – If the tool that’s implemented doesn’t mesh with the system it’s being downloaded with, the app’s performance–and thus the user’s–will be compromised. Compliance problems – If your organization needs to meet certain compliance standards, the presence of unmanaged software makes it almost impossible to meet said standards. Data loss – If IT management doesn’t know that a software is on the network, it won’t be covered by organizational backup strategies, meaning work completed using shadow IT apps won’t be backed up. You can see why IT admins and most decision makers look at shadow IT as problematic. Shadow IT is Good There aren’t too many issues in life that are dialectically bad. There is always a bit of positive with anything, including shadow IT. Recently, there has been a shift in the way that some organizational leaders and IT professionals look at shadow IT. You see, businesses are always looking to increase productivity, to get the most out of their available capital, to find solutions for problems. Shadow IT, for all its problems, allows workers to accomplish all three of these fundamental goals; and, it seems IT admins are coming around. According to a study of 1,000 IT professionals, 77 percent believe that embracing shadow IT solutions can help a company innovate quicker than their direct competition. That’s not all. 49 percent said that shadow IT boosts productivity. 45 percent said that shadow IT helps promote employee engagement. 40 percent said that shadow IT helps promote adherence to IT security requirements. 40 percent said that shadow IT would help reduce employee turnover. This survey seemingly splits the IT community in half, with half believing shadow IT to be an active menace and half believing there are strong benefits to promoting the use of some shadow IT resources. Now, I […]
As a managed service provider, these tools are fairly critical to our own operations. How We are Able to Operate One of the defining characteristics of managed services is the practice of monitoring the IT solutions that our clients utilize in order to proactively detect and resolve issues. This is accomplished through the use of a set of tools and software titles that give us the ability to remotely track your complete IT infrastructure and resources. With the sneak peek that these tools provide us, we can create a comprehensive record of data that we can always turn to for reference. This ultimately gives us a huge repository of data, all dedicated to improving your experience with your IT, including: Each and every device you have, from your network infrastructure to every company-owned endpoint and peripheral that attaches to it. The proper configuration for each of these devices. The date that each of these devices was installed. The licenses that your business needs to maintain, and the status of the ones you have. A comprehensive history of all service that each of these devices has received. Putting this record to use, we have the information we need to identify upcoming and current issues you may encounter, reducing the number of interruptions and challenges your business needs to deal with – preserving your productivity and contributing to your success. Want to learn more about our services? Reach out to us to start off with a network audit, which gives us an idea of what your current strengths and weaknesses are, where technology is concerned. Schedule one today by calling (831) 758-3636.
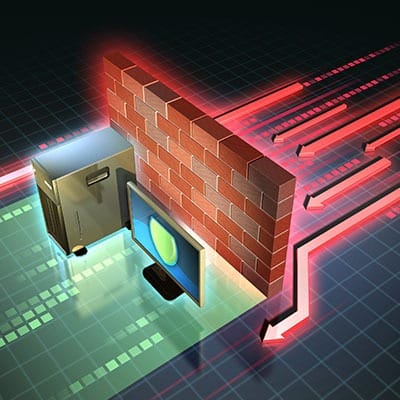
Let’s take a closer look at what a firewall is, and how they help to protect your assets. Defining Firewall A firewall is something that helps keep threats and malicious entities from coming into your computer or computer network from the Internet by monitoring and controlling traffic, both incoming and outgoing. Named for the real-world barrier that is used to impede the spread of fire throughout a structure, a firewall prevents these threats from spreading in a similar fashion. These solutions are available as both hardware-based and software-based systems, and different types are available that focus on different needs and functionalities. How a Firewall Works The firewall uses a barrier of code to ensure that there is some separation between your computer or network infrastructure and the larger Internet, examining data packets as they arrive and deeming whether or not they can continue. The Difference Between Software-Based and Hardware-Based Other than the obvious difference in how they are deployed, there are some differences between software and hardware firewalls that are important to address. Hardware Firewalls A hardware firewall is a device that integrates into a network to protect it, and is often built into broadband routers. These firewalls focus primarily on inbound data and information, comparing traffic to preset conditions to deem whether or not that data will be allowed in. While this variety is very common in homes and small businesses – primarily due to its simplicity and its ability to connect to multiple devices – it does have one considerable shortcoming. Hardware firewalls only analyze incoming data. As a result, the firewall won’t detect certain, considerable issues, like if a computer has been infected and assimilated into a botnet. Software Firewalls While they serve effectively the same purpose, software firewalls have more or less opposite strengths and weaknesses. As a software firewall is installed on an individual endpoint, it only serves to protect that one device. However, it also monitors all traffic (incoming and outgoing), enabling it to identify and stop more threats. One of the biggest benefits of a software-based firewall is that it can be customized to each user, as it only covers that user’s workstation. So, if one of your users needs more forgiving permissions than the rest of your team, you can allow for them by using a software-based firewall. Why Not Use Both? To maximize your firewall-based protections, we recommend that you use both hardware-based and software-based firewalls. This assists your security twice as much, without causing any interference between the two. Combining their protections, along with implementing other key security features and tools, can help keep your business optimally secure. In fact, modern Windows operating systems come with a built-in firewall. While this protection doesn’t stop everything, when combined with managed security on the rest of your network, it serves an important part of your overall security. We can help. To learn more about the security and productivity assistance we can offer, reach out to SRS Networks at (831) 758-3636.
Over the last three or four years, we’ve seen some of the world’s biggest data breaches. Yahoo, Marriott-Starwood, and Equifax were the highest profile attacks, with a combined 3.5 billion accounts hijacked for those events on their own. To put that in perspective, you could take any two human beings on the planet, and there would be a pretty good chance that one of them was a victim of a data breach over the last three years. Security breaches like this have increased by over 67% since 2014, and the trend is still climbing. What’s at Stake? We’re Basically All Hacked Now? It’s actually almost a good thing that these massively high-profile data breaches are happening. Hear me out: It brings this type of crime to the public eye – Most Americans know about the Equifax breach. Awareness is a huge step in the right direction. There is so much data in these breaches that it is practically impossible for cybercriminals to use it all – If 500 million credit card numbers are stolen, the chances of one in particular being used goes down substantially. We’re not looking at data breaches in a positive light, but I firmly believe that the last few years has been the lesson the world needed, and it is a lesson a lot of organizations are taking very seriously. Policies and laws are hitting the books, and compliance regulations are being mandated within certain industries. Organizations of all sizes are taking data security seriously. What Does This Mean for Smaller Businesses? Of course, when we talk about data breaches, we always reference the big ones like Yahoo, Target, Sony, eBay, etc. Or we talk about the municipal attacks, where large cities like Albany, NY and Baltimore, MD were targeted, along with smaller towns like Wilmer, TX and Lake City, FL being held at ransom. We don’t hear about the 40-person company that goes under because of a cyberattack, because it affects fewer people. The problem is that small businesses are a major target. In fact, according to a survey by Verizon, 43% of breach victims were small businesses. Smaller businesses are easier targets because they usually don’t pay as close attention to their security. It’s Time to Take Cybersecurity Seriously There are things you can do. If you want to start getting serious about your organization’s cybersecurity, there is no time like the present. Call our knowledgeable IT professionals at SRS Networks today at (831) 758-3636 to get started taking the steps you need to keep your company’s data and infrastructure secure.
Rotating Pages You’ve probably encountered this: You get a PDF and open it only to find that the document is upside down. It might not be a huge issue, but you’d really prefer that it was right-side-up. To fix this, many PDF viewing programs like Adobe Acrobat Pro offer options to rotate the document. If you’re using Acrobat Pro, the Rotate Pages option can be found under the Document menu. Once opened, you can select the pages that you want to be rotated, and how they should be rotated. Some of the other PDF readers offer a quick button in the toolbar that allows you to rotate each page individually. Regardless of how you choose to get it done, rotating pages just makes reading them simpler. Signing PDFs These days, PDFs are routinely sent that need signatures, whether it’s to view the document, or because it is a contract of some type. For years, people would print out the document, sign it, and scan it back over to complete this task. Today, there is a solution that lets the recipient avoid the printer altogether. It’s as simple as downloading some free software, such as Adobe Reader. Once you download it, signing documents is relatively simple. With the PDF open, click on the Fill & Sign button, then Sign, and finally, Add Signature. At this point, you’ll have three options: Type – You type your name to indicate that you have seen the document, and an electronic signature is rendered (which almost certainly will not resemble your actual signature). Draw – Using your mouse as you would a pen, you draw your signature in the space provided. Image – You use a scanned image of your actual signature that is then saved for future use. At that point, just make sure your signature is positioned where it needs to be, click apply, and save. These days, many line-of-business applications produce signable PDFs to make contracts move faster. Password Protection There are times when you want to control who can (and more aptly who can’t) see a particular PDF. Make sure that any password you set up for PDFs are distributed through secure channels to avoid the document from being breached. Microsoft Word allows you to turn a file into a PDF by using the “Save as” function. All you have to do is select “PDF” as the file type. Before you click Save, you will be able to find a More options button, which will open another window, where encrypt document with a password can be found under Options. Selecting this gives you the ability to set a password that anyone viewing your PDF after that point will have to provide in order to open it. Merging Files Once you distribute a PDF, it is easy to lose track of all the different versions. PDFs allow you to consolidate versions to keep track of all the information in one place. You can accomplish this with various paid or free software titles. Pass it by your IT department first, so it doesn’t cause any problems. Assuming you choose Adobe Acrobat, this process is exceedingly simple. All you have to do is access the Tools menu and click on Combine files. Then, after you have used Add Files… to assemble all the PDFs […]
What Is Your Data Worth? Whether you actively use it, or it just sits here, your data is worth quite a bit to your company. After all, your data is made up of a combination of all the work that your people have done, marketing information filled with PII, and sensitive information of your staff, prospects, and clients. What would happen if that data were to get stolen or lost? Let me tell you what it would mean by telling you a story. A nameless business rents out office space on the corner of two very busy streets. One day, shortly after everyone in the office had gone home for the day, a man driving a truck out of control, jumped the curb and ran directly into the building, destroying the company’s entire server room. The first thing you may think is, “Is he okay?” The second thought you have should be, “What does that have to do with their cybersecurity?” Hold that thought. In one scenario, the company has just onsite backups and when the truck blasts through the building’s facade and into the server room, those onsite backups are no use against the force of a runaway truck. All the hardware in the server room is destroyed. In another scenario, the company uses a BDR to back their data up and in the cloud, when the truck blasts through the server room, the hardware is destroyed, but the data is still available, backed up in the cloud. This business survives while the other fails. That right there is why the BDR is superior. How BDR Fits Into Cybersecurity Strategies For some, the retention of data would be value enough out of a BDR, but for an organization that is concerned as much in the continuity of their business as they are on the security of their data, the BDR offers a way to secure critical data outside your organization’s network. Cybersecurity strategies dictate that all data that is vital to the sustainability and continuity of your business be stored in multiple places; specifically, outside of your network. The BDR with its ability to push data to outside data centers fulfills this requirement, and helps promote data security. Furthermore, because the backups are stored offsite and outside the network, it works as a failsafe against critical situations like a ransomware attack. If you would like to ensure that your data is secure and available in the case of a disaster, whether it be a runaway truck crash or ransomware, contact the IT consultants at SRS Networks to talk about getting your organization a BDR. Call us today at (831) 758-3636 for more.