Regardless of what your business does, or how it does it, the data your business has is valuable. After all, a lot has gone into its creation… just consider the combined effort that your sales and marketing team, your human resources department, and the rest of your staff rely on and generate during their respective operations. Add to that all the data you’ve collected from your clients and customers. Now imagine the repercussions of losing any of that data. So Yes, Data is a Big Deal… … and as such, it needs to be protected. While antivirus, firewalls, intrusion detection, and all the other security tools we always recommend are a necessary part of this, a real disaster will require more. It will require a comprehensive backup and disaster recovery strategy to be fully planned and implemented. Of course, a “disaster” can come in many forms, like: Human error Malware attack Sabotage and theft Hardware malfunction Power surges Software corruption So, with all of the different ways that your business could experience disaster, it is imperative that you create a business continuity strategy that, by incorporating a backup and recovery plan, prepares you to sustain your operations through even the worst possible scenarios. In theory, a business has options to consider when making these preparations. Technically speaking, backup solutions like tape and removable hard drives could work for you, as could a cloud backup. At the end of the day, it all comes down to how your data is handled, and how you would need to scale your backup in the future. Having said that, we typically recommend a BDR solution. This is because the BDR covers both your backup and disaster recovery needs. As a network-attached storage device, it is configured to incrementally backup files, preventing the large chunks of data created between backups from being lost. The BDR can also act as a temporary server, should your original experience malfunctions. To provide the needed redundancy, the BDR will also save a copy of your backup in an offsite data center. As a result, a disaster that wipes your business’ data as well as the BDR still won’t eliminate your data entirely. To learn more about the BDR, reach out to SRS Networks by calling (831) 758-3636.
Office 365 Mobile Office 365 is a cloud-hosted version of Microsoft’s award-winning Office productivity suite. This provides users both a cloud version and a downloadable version of the software for multiple devices. Realizing that the future of the product is likely going to have to embrace mobility, Microsoft has been aggressively developing the software for mobile devices. For years, you could get Word, Excel, PowerPoint, OneNote, OneDrive and Outlook through dedicated apps on your smartphone or tablet; and, they work well, but it could often be a cumbersome experience to receive files, find them, and access them quickly. This is no longer the case. In response to complaints about a lack of concrete file management, Microsoft has built the Office Mobile app for Android and iOS. This new app automatically gives the users a list of any Microsoft Office document, spreadsheet, presentation, or note. Better yet, once you tap on a file, it opens it in the corresponding application on your phone. This not only allows you to have quicker access to your resources, it also provides the following options: Transfer Files – Users can share files between their computers and their phones. Share Nearby – Using the app (and NFC), you can transfer and receive files by just being in the proximity of another user that is using the app. Convert Text in Images – Users can extract text from a picture or extract a table from a picture into a spreadsheet. More with PDFs – The Office Mobile app allows users to do much more with PDF files. They can convert documents into PDFs, sign a PDF, and use pictures to build a PDF in multiple ways. Scan a QR Code – You can use the Office Mobile app to scan a QR code and save it into OneNote. The Office Mobile app also gives users options to create quick notes, use Microsoft Lens to capture information, or create new Office documents of all types. The Office Mobile app is available on the Apple App Store and Google Play Store, and is free to download. If you already have a logged in Microsoft Office 365 account on your phone, the Office Mobile app will automatically propagate with your available information. If you don’t already have Microsoft Office 365, and would like to talk to someone about gaining productivity and efficiency with some of the best productivity software on the market, give SRS Networks a call at (831) 758-3636 today.
What Software-as-a-Service Really Is To really get a handle on SaaS and its benefits, let’s examine it in what is likely its most well-known utilization: the streaming services offered by Netflix. Really, Netflix streaming effectively works the same way that SaaS works for organizations that make use of it. Subscribers to Netflix’s streaming service pay a monthly fee to access a shifting library of content as much as they want, on a variety of devices. Similarly, SaaS allows businesses to utilize up-to-date versions of crucial business programs, also billed on a month-to-month basis. This results in additional similarities, which translates positively for the user. The Benefits of SaaS Accessibility Netflix enables its users to view content from practically anywhere, provided they have an account, a compatible device, and a connection to the Internet. SaaS works in the same way, opening a business to greater opportunities to productivity. Scalability As a bonus, both options can easily be scaled to better fit one’s needs… a Netflix account can be shared between up to five user profiles, and different tiers allow different numbers of profiles to be used simultaneously. As for SaaS, an agreement can usually cover as many users as a business would need, allowing for new hires, departing employees, or shifting responsibilities. Cost Efficiency Now, you may be thinking that it would ultimately be less expensive to simply procure a given software solution and maintain it in-house. However, you need to consider the additional investments that this approach will require of you… like acquiring and maintaining the hardware needed to support these solutions. These costs alone would almost certainly negate any “savings” you’d see from managing your software yourself. Security Using older software that isn’t kept up-to-date can lead to vulnerabilities. The SaaS model means the software is always kept secure via regular updates from the developer. California businesses can rely on SRS Networks for a wide assortment of their IT needs, including SaaS. Learn more about what we offer by calling (831) 758-3636 today.
VoIP Allows You to Do More While a VoIP system is, at its core, an alternative to the traditional phone solution, most VoIP options can provide you with far more capability than a traditional phone system. For instance, many VoIP options provide capabilities like instant messaging, conferencing, and call recording. VoIP is More Secure When comparing the two options, VoIP is far more secure to use than the traditional landline. This is because, rather than the analog approach that telephony has historically taken, the digital data that VoIP sends can use encryption. This protects all information transmitted through the system. VoIP is More Portable Instead of being tied to a set location, as the traditional business telephone system would be, VoIP can be accessed from anywhere the Internet can be. What’s more, as many VoIP solutions have an associated mobile app, it plays nice with smartphones – allowing your employees to use their mobile device to communicate with business contacts, without disclosing their personal numbers. VoIP Offers Automated Client Interaction While communicating with your clients and assorted contacts is important, it is just as important that your employees aren’t constantly distracted by their work by fielding phone calls, if they can help it. VoIP solutions can be configured to support a variety of options. These options include an automated menu to give a caller more information at any hour, a directory to help a caller reach their desired contact, or even the option to forward calls to an employee’s mobile device so that truly urgent calls can be answered at any time. This is just a brief sample of the many ways that VoIP provides businesses with operational (and yes, financial) benefits. To learn more, or to ask any other business IT-related questions, reach out to the SRS Networks team at (831) 758-3636.
Let’s begin by defining what a CRM strategy really is, which will help to illustrate why it matters. The Concept of a CRM Strategy Using CRM software has a pretty low bar for entry. Basically, you just have to procure it and populate it with the data you have collected. The purpose of a CRM strategy is to really use your solution to the fullest extent that you can, which allows you to optimize your outcomes. There are a few ways that your CRM strategy can enable you to do so: It condenses data in context to help you reference it as you make decisions and set goals. It makes customer service efforts more comprehensive, which can boost retention and loyalty. It assists you in making sales by scaling your process properly and eliminating redundancy. Naturally, these are benefits that can assist any business in its pursuit of its goals, so it is important that you create a proper CRM strategy to guide you. Here is a simple process for you to follow: Understand Your Goals and Strategize For ThemWhat is it, exactly, that you want your business to accomplish? What is your intended use of your CRM software, and what do you want to achieve with it? How will each department use it to do strive toward their goals? How will your offering be distributed? Once you have conferred with your team and answered these questions, it is time to consider the business landscape and who your ideal clients are. Then, determine what makes your offer different, and commit to providing this difference each time in the way that best suits your prospects. Analyze and Organize Your TeamHow will the introduction of your new CRM software impact your team? Speak with those whose job responsibilities will be affected by your new solution, and look for any past experience with such platforms for their impression of different options. You will also need to identify those team members who will be using the software to collaborate and be sure that everyone understands their particular roles. It is also helpful to determine the goals that each department should strive toward, and identify the key performance indicators that will help measure their progress. Implementing Your New Solution and StrategyDetermine how different contacts will be divided within your CRM, and establish a policy of collecting all the information you need from a contact that is going to be included. You should also strongly consider mapping out your sales processes for each of your services so it is easier to manage your brewing business. It is also a good idea to keep your software requirements in mind when selecting your CRM, as you will want to select a title that plays nicely with your existing solution. Is your chosen email platform Outlook? Make sure to find a CRM that integrates with it for optimal benefits. SRS Networks is here to help you with these considerations, and more. To learn what we can do to assist your customer relationship management through IT solutions, or any other of your business processes, reach out to us at (831) 758-3636.
Samsung Galaxy s10 Plus Widely regarded as the best phone on the market, the Samsung Galaxy s10 Plus improves on the remarkable Galaxy s9 Plus across the board; improving on form factor, processing, camera, and battery. The device is Gorilla Glass 5 on top of an aluminum frame and weighs in at 6.17 oz. The display comes in at 6.4 inches and uses most of the phone’s available real estate. The form factor of the device has had a bit of a renovation, featuring sharper edges than previous models. Inside the device, the Galaxy s10 Plus has a Qualcomm Snapdragon 855 processor with 8-to-12 GB of RAM and storage capabilities that range from 128 GB to a full terabyte. The Galaxy s10 Plus features three rear-facing cameras, including a wide angle, ultra wide angle, and a telephoto option. Samsung also increased the battery to a solid 4,100 mAh. It is shipped with Android 9 Pie, but some carriers already deliver an upgrade to Android 10. Available in Prism White, Prism Black, Prism Green, Prism Blue, Canary Yellow, Flamingo Pink, Ceramic Black, Ceramic White, Cardinal Red, and Smoke Blue this device can be had on most carriers for between $799 and $1,199. Samsung Galaxy s10 PlusBody: Aluminum frame with Gorilla Glass 6 front, Gorilla Glass/Ceramic backDisplay: 6.4-inch Dynamic AMOLED (~522 ppi)OS: Android 9.0 with Samsung One UI skinChipset: Qualcomm Snapdragon 855Memory: 128 GB/8 GB RAM; 512 GB/8GB RAM; 1 TB/12GB RAMExpandable Memory: microSD up to 1 TBCameras: Three back-facing (12 MP, 26mm wide angle; 12 MP, 52mm telephoto; 16 MP, 12mm ultrawide); Two front-facing (10 MP, 26mm; 8 MP, 22mm)Sounds: Stereo speakers, 3.5mm headphone jackBattery (battery endurance rating): 4,100 mAh battery (91 hours)Security: Ultrasonic, under display fingerprint reader; IP 68 resistantMiscellaneous: Nano-SIM, Wi-Fi 6, Bluetooth 5.0, 15W fast charging, wireless charging, reverse wireless charging, NFC, FM RadioOther versions: Samsung Galaxy s10, Samsung Galaxy s10e Apple iPhone 11 Pro Max This year Apple’s flagship is called the iPhone 11 Pro Max and it continues Apple’s dedication to creating elite-level smartphone experience. The iPhone 11 Pro Max is glass front and back, built on a stainless steel frame and providing users a 6.5-inch Super Retina display. Inside the device there is Apple’s proprietary A13 Bionic chip, four GB of RAM, and either 64 gigabytes or 512 gigabytes of onboard storage. The biggest improvement over the iPhone XS are the cameras. Users will have the use of three 12-megapixel lenses including an ultra-wide angle lens, a wide angle lens, and a telephoto lens. The device runs on the iOS 13 operating system and can be had from most major carriers in Space Gray, Gold, Silver, and Midnight Green for around $1,100. Apple iPhone 11 Pro MaxBody: Stainless steel frame with glass front/backDisplay: 6.5-inch Super Retina XDR OLED; 1,242 x 2,688 (~458 ppi)OS: iOS 13Chipset: Apple A13 BionicMemory: 64 GB/4 GB RAM; 256 GB/4 GB RAM; 512 GB/4GB RAMExpandable Memory: NoneCameras: Three back-facing (12 MP, 26mm wide angle; 12 MP, 52mm telephoto; 12 MP, 13mm ultrawide); Two front-facing (12 MP, 23mm; SL 3D camera)Sounds: Stereo speakersBattery (battery life): 3,969 mAh (102 hours)Security: Face ID, IP 68 resistant Miscellaneous: Nano-SIM, Wi-Fi 6, Bluetooth 5.0, 18W fast charging, wireless charging, NFCOther versions: Apple iPhone 11, Apple iPhone 11 Pro Samsung Galaxy Note 10 Plus Years away from the […]
Shadow IT is Bad Let’s face it, most people working today have been using technology for over 20 years. They may not be IT experts (they aren’t), but they aren’t novice users either. They can spot a tool when they see one. For the end-user, finding solutions to their problems in the form of a simple-to-download application, is a no brainer, especially if the person is proficient with the unauthorized software. They won’t think twice before downloading the title. The problem, quite obviously, is that the software being downloaded may have vulnerabilities upon download; and, if it’s allowed to fester without updates on a workstation for some time, will likely have some. Unfortunately, vulnerable software on a network endpoint is a hole in the network itself. We spend a lot of time on this blog talking about cybersecurity, and one of the big no-nos is leaving unpatched holes in your network by not frequently patching and updating software. Since the IT department or managed IT provider handles this process, if they don’t look for a software to update (because they often don’t know it is there), it will likely be a problem before long. What are the potential risks? There are a multitude. They include: A lack of security – Without the visibility and control over network-attached resources, IT management becomes much more difficult. If there is a potential that a piece of software can put a hole in your network, you are compromising the network’s security. Problems with performance – If the tool that’s implemented doesn’t mesh with the system it’s being downloaded with, the app’s performance–and thus the user’s–will be compromised. Compliance problems – If your organization needs to meet certain compliance standards, the presence of unmanaged software makes it almost impossible to meet said standards. Data loss – If IT management doesn’t know that a software is on the network, it won’t be covered by organizational backup strategies, meaning work completed using shadow IT apps won’t be backed up. You can see why IT admins and most decision makers look at shadow IT as problematic. Shadow IT is Good There aren’t too many issues in life that are dialectically bad. There is always a bit of positive with anything, including shadow IT. Recently, there has been a shift in the way that some organizational leaders and IT professionals look at shadow IT. You see, businesses are always looking to increase productivity, to get the most out of their available capital, to find solutions for problems. Shadow IT, for all its problems, allows workers to accomplish all three of these fundamental goals; and, it seems IT admins are coming around. According to a study of 1,000 IT professionals, 77 percent believe that embracing shadow IT solutions can help a company innovate quicker than their direct competition. That’s not all. 49 percent said that shadow IT boosts productivity. 45 percent said that shadow IT helps promote employee engagement. 40 percent said that shadow IT helps promote adherence to IT security requirements. 40 percent said that shadow IT would help reduce employee turnover. This survey seemingly splits the IT community in half, with half believing shadow IT to be an active menace and half believing there are strong benefits to promoting the use of some shadow IT resources. Now, I […]
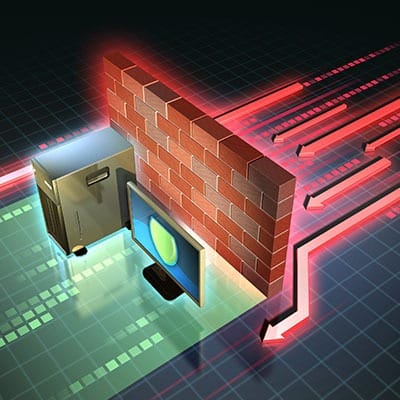
Let’s take a closer look at what a firewall is, and how they help to protect your assets. Defining Firewall A firewall is something that helps keep threats and malicious entities from coming into your computer or computer network from the Internet by monitoring and controlling traffic, both incoming and outgoing. Named for the real-world barrier that is used to impede the spread of fire throughout a structure, a firewall prevents these threats from spreading in a similar fashion. These solutions are available as both hardware-based and software-based systems, and different types are available that focus on different needs and functionalities. How a Firewall Works The firewall uses a barrier of code to ensure that there is some separation between your computer or network infrastructure and the larger Internet, examining data packets as they arrive and deeming whether or not they can continue. The Difference Between Software-Based and Hardware-Based Other than the obvious difference in how they are deployed, there are some differences between software and hardware firewalls that are important to address. Hardware Firewalls A hardware firewall is a device that integrates into a network to protect it, and is often built into broadband routers. These firewalls focus primarily on inbound data and information, comparing traffic to preset conditions to deem whether or not that data will be allowed in. While this variety is very common in homes and small businesses – primarily due to its simplicity and its ability to connect to multiple devices – it does have one considerable shortcoming. Hardware firewalls only analyze incoming data. As a result, the firewall won’t detect certain, considerable issues, like if a computer has been infected and assimilated into a botnet. Software Firewalls While they serve effectively the same purpose, software firewalls have more or less opposite strengths and weaknesses. As a software firewall is installed on an individual endpoint, it only serves to protect that one device. However, it also monitors all traffic (incoming and outgoing), enabling it to identify and stop more threats. One of the biggest benefits of a software-based firewall is that it can be customized to each user, as it only covers that user’s workstation. So, if one of your users needs more forgiving permissions than the rest of your team, you can allow for them by using a software-based firewall. Why Not Use Both? To maximize your firewall-based protections, we recommend that you use both hardware-based and software-based firewalls. This assists your security twice as much, without causing any interference between the two. Combining their protections, along with implementing other key security features and tools, can help keep your business optimally secure. In fact, modern Windows operating systems come with a built-in firewall. While this protection doesn’t stop everything, when combined with managed security on the rest of your network, it serves an important part of your overall security. We can help. To learn more about the security and productivity assistance we can offer, reach out to SRS Networks at (831) 758-3636.
Why Is Everyone Swiping? When payday comes once a week or once every two weeks, how do you receive your paycheck? More than half of the US utilizes and relies on direct deposit. It’s no wonder cash has become a scarce payment method. Convenience is such a powerful underlying reason to ditch cash payment. What are the pros, and what are the cons to this convenience? Let’s first talk about some of the pros. Security! Surely, not carrying a wad of cash in your pocket is a more secure method, right? Well, that depends on the type of card you’re carrying as well as the coverage the lender has agreed to. If you have ever hidden something of value from yourself such as your license, cash, your wallet, or even car keys, then you know how it feels to be worried about your belongings. If you’ve ever fully lost one of these objects, you’re not the only one. So how would you proceed if you lost a few hundred dollars cash that was in your wallet? Well, this is where you discover the fact that a credit card is typically a superior payment method. Borrow protection has become a standard in most lender scenarios. Most banks are FDIC (Federal Deposit Insurance Corporation) covered. Yes, in 1933 and even sometimes today, people had a hard time trusting banks with their money. These mattress-stuffers have failed to realize that in nearly every case your money is actually covered by insurance. With a credit or debit card, that few hundred dollars you lost would never actually leave the comfort of your bank account. If some sort of fraudulent activity occurs where money actually disappears from your account for an unauthorized reason, lenders today are able to refund you while disabling the existing card, preventing recurring theft. How Else are Cards Protected? Credit and debit card utilization has caused strict standards of security to be implemented anywhere that accepts these forms of payment. These standards are referred to as the Payment Card Index Digital Security Standard, or PCI DSS. This mandates all businesses to protect data collected about the cardholder. This includes any and all information found on the user’s card. This information should NOT be stored, unless recurring billing or some other product or service improvement has been negotiated with the cardholder. Here are some other protection methods which further prove the benefit to leaving cash at the bank: Dynamic Card Verification Values – Your CVV value is what can prevent someone from taking a picture of your credit card as you pull it out of your wallet from actually being able to make purchases with it. This value on the back of most payment cards adds that extra layer of security that could foil a determined thief. As technology changes, even these CVV often feel the effects. Today, some lenders provide cards that utilize a different value for each time of day. Mobile Wallet – While most of us have seen commercials of someone paying for goods or a service simply by holding their smartphone up to the reader, this technology has evolved into far more than a gimmick. This method of payment, if handled properly, can be an extremely convenient and secure means to purchase things. Biometrics – Biometric technology has […]
How Many Devices Are On This Network? When your business was first put together and you initially started out, you could very well have been using technology in one way, and it could have been very different than what you are doing now. This means that the infrastructure that was first put into place may not have allocated resources appropriate for what you are trying to accomplish. Ignore what you needed in the past – what do you need now? How many users need to connect to the network… and how many devices will that equate to? Many devices now connect to the Internet to function, and how many devices are involved with your business that also connect to its Wi-Fi, like point-of-sale systems or wireless printers? You may be overtaxing your wireless network. One easy fix is to hardwire the things that can be, freeing up the wireless. What Processes Need to Be Supported? What is it that you need your wireless network to do, exactly? Based on these needs, you may need to adjust your business’ infrastructure to match – down to the kind of router you’re using. Different models of routers offer different features. Our IT experts are here to make sure you get the appropriate equipment for your particular situation – the first time. How Secure is Your Internet? As critical as the Internet is for many businesses to be able to operate, it is also a great tool for many criminals trying to take advantage of these businesses. Using networking equipment that helps to prevent these kinds of issues with built-in protections like firewalls and antivirus certainly helps. The professionals here at SRS Networks are ready to help you determine exactly what your business needs. To learn more, reach out to us at (831) 758-3636.